Model Driven Development of Security Monitors (CASED I)
Note: CASED I has ended in 2012.
This research is located in the subproject Secure Things that deals with security of embedded systems. We are developing a development process, which allows automatic generation of software and hardware security monitors from specifications of the requirements phase. These monitors will be able to observe messages or system calls that are sent and received from the embedded systems to recognize possible attacks. Later, reasonable reactions to attacks should be performed that allow systems to reconstitute themselves.
The figure below shows the targeted process, based on model-based graphical languages, to generate the security monitors. First, requirements are modeled as use and misuse cases that complement to each other. Misuse cases are related with their use cases. For every use case and misuse case, one or more Live Sequence Charts (LSCs) are constructed that describe either scenarios of the use- or misuse case. These specifications should not depict the implementation of the use cases, but the general sequence of messages or system calls. In the next step, we combine the LSCs of the use and misuse cases into Petri net like intermediate language - the Monitor Petri nets (MPNs). These nets have special places and a deterministic execution semantics. After this step, the generated MPNs together with the aid of system-/platform-specific information are used by a code generator that generates the implementation in e.g. C or VHDL. Before code generation optimization techniques should be applied to the MPNs to reduce the size of the nets by removing and merging places and transitions.
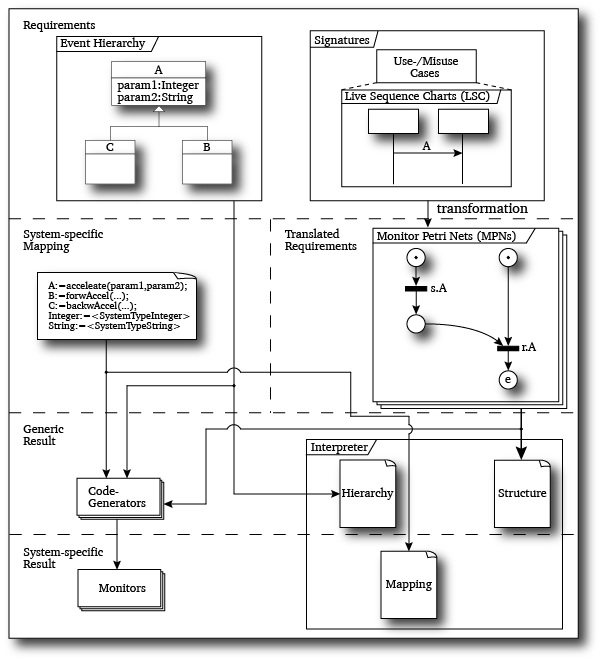
Figure 1: Monitor Generation Process
Related Dissertations
- S. Patzina: "Entwicklung einer Spezifikationssprache zur modellbasierten Generierung von Security-/Safety-Monitoren zur Absicherung von (Eingebetteten) Systemen.", Technische Universität Darmstadt, 2014, URL: https://tuprints.ulb.tu-darmstadt.de/4132/.
- L. Patzina: "Generierung von effizienten Security-/Safety-Monitoren aus modellbasierten Beschreibungen.", Technische Universität Darmstadt, 2014, URL: https://tuprints.ulb.tu-darmstadt.de/4133/.



